Monetary Privacy: The Last Bastion of Human Dignity
“He who does not move does not feel his chains.” Rosa Luxembourg’s phrase resonates strangely in the digital age. Digital currency today reveals invisible chains that many still do not perceive. Cash quietly disappears, replaced by a world recorded, analyzed, and continuously interpreted. Every transaction becomes data, and every data a lever of control. Privacy is no longer a moral luxury but a political fault line. Institutions defend transparency as a condition of stability. Freedom advocates see privacy as a fundamental guarantee. This tension reshapes our relationship with power, trust, and individual autonomy. The central question no longer only concerns technology but what we accept to reveal in order to exist. This text explores the existential battle of monetary privacy: protecting human dignity when everything becomes traceable.
In Brief
- Digital currency redefines the border between individual freedom and institutional control.
- Financial privacy protects dignity in a fully traceable world.
- The phrase ‘I have nothing to hide’ denies our natural needs for intimacy and protection.
- Financial surveillance constitutes the deepest form of mass surveillance.
- Every expenditure reveals an intimate part that no one should exploit without necessity.
- The monetary trilemma opposes transparency, auditability, and privacy in any digital system.
- Transparency protects collective probity, but must never become individual surveillance.
- Financial privacy becomes a technological counter-power against the expansion of control systems.
- Secondary layers offer selective privacy, compatible with public transparency.
- Healthy monetary policy requires limited auditability, distributed governance, and public rules.
- The ideal model is inspired by Bitcoin: transparent at its foundations, protective in its uses thanks to secondary layers.
The Right to Privacy: We All Have Something to Hide
Everyone knows someone who claims to have “nothing to hide.” The phrase seems reassuring but rests on a dangerous illusion. It assumes a world divided between innocents and guilty, where morality is perfectly binary. In reality, accepting to be constantly visible means accepting to be reducible, predictable, almost insignificant. It says: “My privacy matters so little that power can see everything without ever bothering me.” Yet, our daily actions tell the opposite. We close our doors, protect our passwords, encrypt our messages. Even the staunchest supporters of surveillance instinctively defend their private space, revealing the central contradiction of their discourse.
Human beings need a vital double movement: to be seen to exist, and to be hidden to remain free. We share a part of ourselves and preserve another. Even those who think themselves transparent bear silent battles. Perhaps they face a serious illness they would only share with their doctor. We all have something to hide, not out of shame but because intimacy protects our humanity. Without this private space, our behaviors freeze: we become cautious, conformist and fearful. Inner freedom withers when every gesture can be observed.
Continuous surveillance erects an invisible cage. It does not strike but shapes: everyone adjusts their words to avoid judgment. Gradually, creativity contracts, dissent disappears, and shame becomes a tool of governance. Where privacy disappears, human dignity fades in polite silence.
Financial Surveillance as the Supreme Form of Mass Surveillance
Freedom is not measured by the silence of obedient citizens but by the space granted to dissidents. Privacy is not a refuge for criminals: it protects those who think differently, contest, or question authority. Claiming that only “suspects” deserve privacy creates a dangerous trap. Such logic may spare us today and strike us tomorrow.
This dynamic appears acutely in the monetary sphere, where transaction surveillance becomes the most effective tool to shape behavior. Financial surveillance constitutes the quietest and deepest form of social control. It reveals not just what you say but what you really do.

Every expense tells an intimate story, often more intimate than a private conversation. It reveals our priorities, relationships, vulnerabilities, and even beliefs. This data is more valuable than words to a power eager to direct society. Media influence shapes opinions, financial control shapes behaviors. When every payment becomes traceable, freedom bends and the implicit norm becomes obedience.
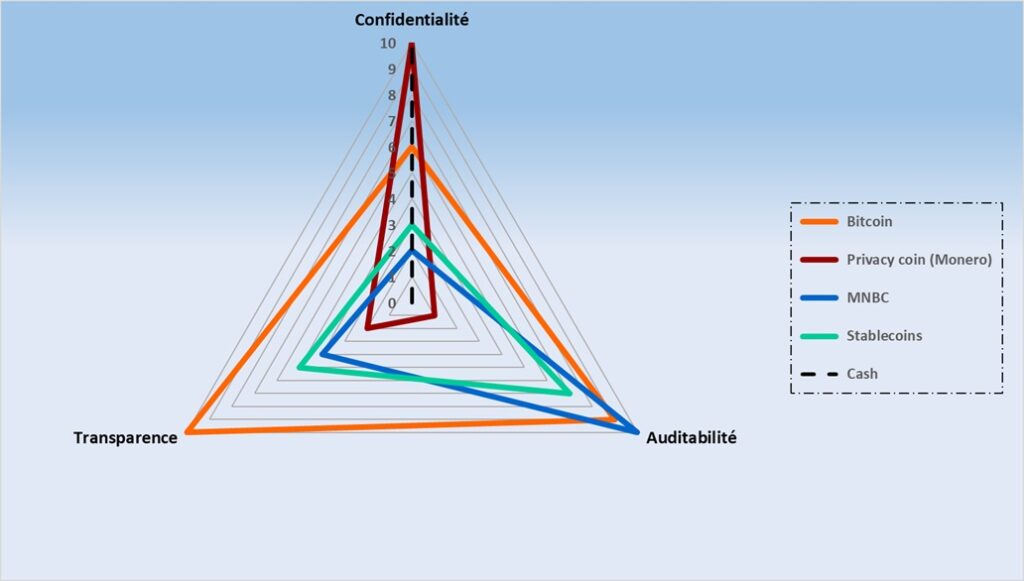
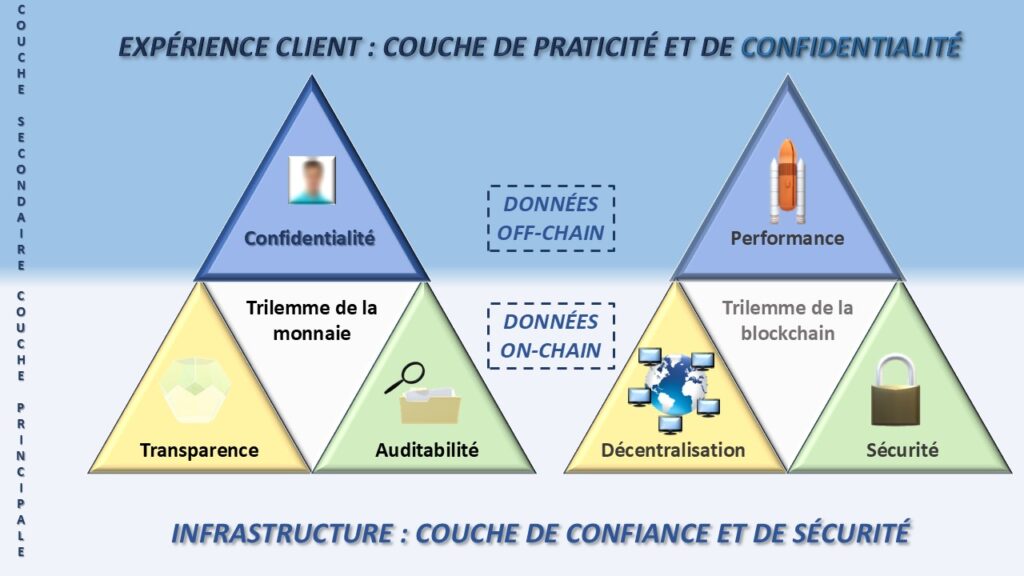
Thus arises the modern monetary trilemma. A currency must be transparent to prevent abuse and verifiable to strengthen trust. But if it sacrifices privacy, it slides toward a surveillance regime. The balance between transparency, auditability, and privacy then becomes a civilizational challenge.
The Trilemma of Money: A Civilizational Choice
Developing a monetary model is like building a house with three incompatible requirements. You cannot want it huge, very cheap, and delivered immediately. One of the three criteria (quality, budget, time) must necessarily be sacrificed. The logic is identical in blockchain architectures, where security, decentralization, and performance struggle for an impossible balance. A digital currency faces a similar tension between transparency, auditability, and privacy. These three goals are legitimate, but achieving them all simultaneously is a balancing act.
Transparency guarantees integrity and limits corruption. Auditability consolidates trust by ensuring clear, shared verification. Privacy protects personal life within a digitized and interconnected environment. The monetary trilemma thus exposes a structural rivalry between control, trust, and freedom. Each system must choose what it prioritizes… and what it accepts to sacrifice.
Transparency and Auditability as Collective Foundations
Transparency is an essential pillar for preventing institutional abuses. It allows verifying the integrity of monetary policies and reduces shadow areas where power abuses lurk. Auditability extends this function by offering accessible and rigorous systemic verification. It ensures that financial flows remain traceable, consistent, and controllable over time. This traceability protects collective stability by providing verifiable evidence indispensable to fighting fraud.

This duo forms the trust foundation necessary for any digital currency and embodies the institutional side of the monetary trilemma. It meets democratic requirements for accountability while strengthening system resilience through controlled information sharing. However, the trilemma shows that strengthening these two pillars reduces space reserved for privacy. This structural tension profoundly influences the design of contemporary monetary systems.
Privacy and Censorship-Resistance as Fundamental Freedoms
Privacy protects the individual in a world where every transaction leaves a digital footprint. It offers an indispensable private economic space for personal freedom by limiting the potential intrusion of dominant economic actors. Censorship-resistance guarantees the ability to transact without prior authorization. It preserves network neutrality against political or financial pressures and protects minorities against potential coercive abuses. Together, these two dimensions constitute the liberal side of the monetary trilemma. However, they come into direct tension with the transparency and auditability needed for collective control.
Each system must decide where to place the cursor between public security and individual autonomy. Bitcoin, Central Bank Digital Currencies (CBDCs), and privacy-focused cryptocurrencies like Monero represent distinct responses to this dilemma. The monetary trilemma highlights the deeply philosophical dimension of digital currency. It reveals a conflict between libertarian values and institutional imperatives, between freedom and control, between privacy and surveillance.
Libertarian Values: Privacy as Freedom
Libertarian thought, heir to the cypherpunk movement, views privacy as an indispensable condition of individual freedom. It asserts that everyone must control the information related to their economic choices. Privacy protects the individual against interference from authorities and overly intrusive private actors. It creates a protected space where transactions neither become surveillance tools nor social discipline mechanisms. For libertarians, a free society rests on the possibility to act without constantly justifying oneself. By limiting institutional power concentration, privacy strengthens autonomy and protects individuals from imposed conformity. Anonymity thus appears as an essential guarantee of personal sovereignty.
From this perspective, a currency is truly emancipatory only if it protects its users. The private cryptocurrency Monero’s protocol pushes this logic to its conclusion. Every Monero transaction is opaque by default, preventing any undue surveillance or economic profiling. This native privacy is not a luxury but an essential defense in a world where data has become a strategic weapon. Monero embodies the pure libertarian vision: privacy is non-negotiable because it protects against political, commercial, or criminal interference.
Monero’s cryptographic mechanisms completely mask amounts and addresses, resembling fundamental properties of cash. However, this protection reduces auditability and traceability and sometimes creates a perception of illicit use. Yet Monero remains the ethical digital reference for financial privacy and a symbol of absolute monetary freedom. It faces increasing exclusions and intense regulatory pressure.
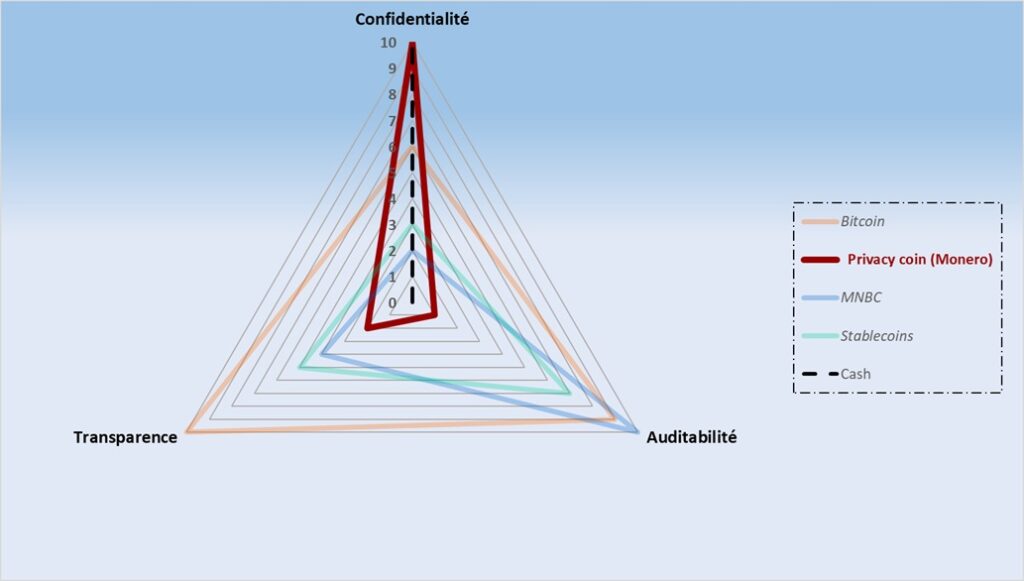
Monero: Total Privacy as a Condition of Economic Freedom
Perfect privacy seems incompatible with digital environments, often synonymous with total traceability. Let’s make a technical parenthesis to understand how Monero bypasses this constraint. In Monero, balances are never publicly visible (illustrations 1 and 2A). The blockchain only displays anonymous mailboxes called outputs, impossible to link to a person. Amounts are masked thanks to cryptographic commitments. The sender identifies their funds using their view key, then spends an output with their spend key (1).
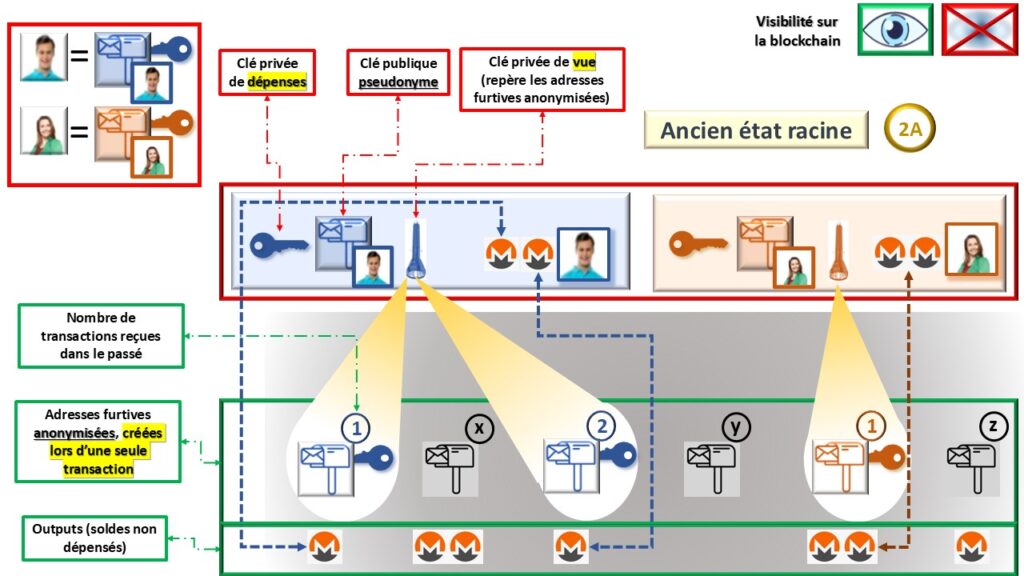
When sending money, they generate a unique stealth address for the recipient (2B). This anonymized stealth address exists only for this specific transaction. Only the recipient can recognize it by scanning the blockchain with their view key (3).
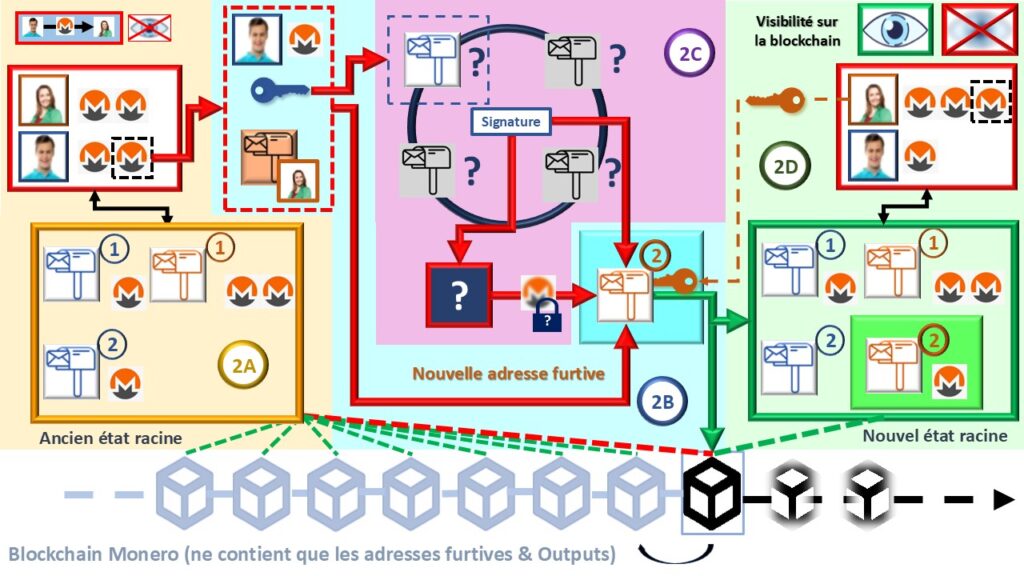
During a payment, the source of funds is also masked. Monero mixes the real output with several others in a ring signature (2C). This signature proves that one of the group’s outputs is spent without revealing which. The blockchain only sees a set of anonymous addresses and an encrypted amount. The recipient, after detecting the stealth address, recovers a new anonymous output they can spend in turn (2D). Thus, no transaction can be linked to an address or identity.

Institutional Values: Privacy as a Risk
Institutions, on the other hand, often perceive privacy as a threat to financial stability and collective security. Too much opacity seems to favor fraud, money laundering, or tax evasion, weakening trust in the economy. Transparency thus appears as an essential condition to protect citizens and guarantee market integrity. It strengthens the ability to detect abuses and prevent behaviors dangerous to society. From this perspective, traceability becomes an indispensable tool to ensure regulatory compliance. Auditability also facilitates supervision and control of sensitive monetary flows. Privacy, seen as an informational blind spot, is then considered a potential obstacle to public order and effective governance.
CBDCs fully embody this institutional preference for transparency and extended transaction control. They offer an unprecedented level of supervision designed to improve resilience and stability of the financial system. But their fully centralized architecture significantly reduces individual privacy and raises concerns about mass surveillance. Stablecoins, meanwhile, take an intermediate position by offering stability and partial transparency. However, their privacy remains dependent on an issuer capable of freezing funds. The rapid adoption of stablecoins in Web3 fuels their success while exposing them to growing regulatory oversight. Their centralized governance also limits their neutrality and makes them less resistant to censorship than decentralized cryptocurrencies.
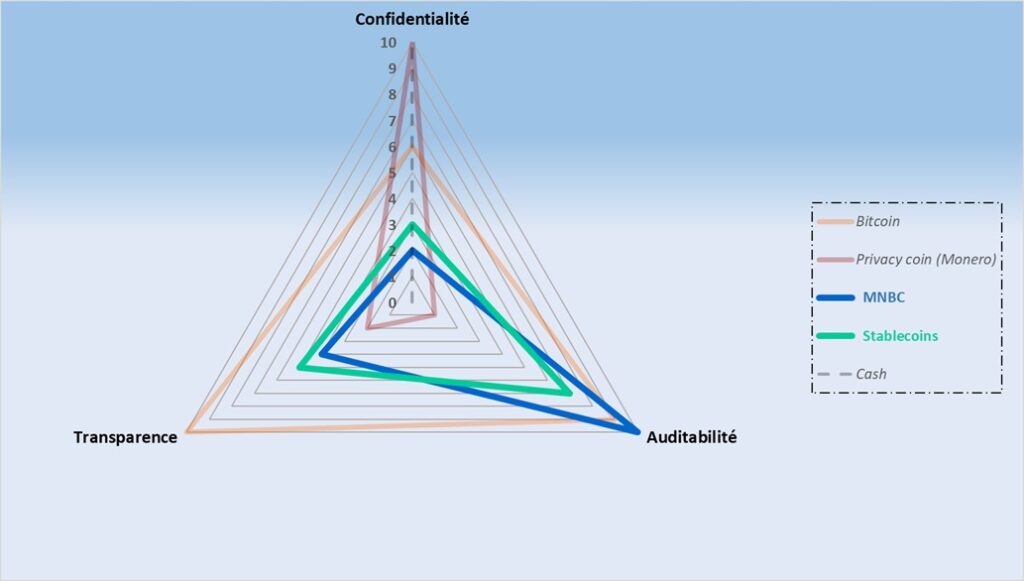
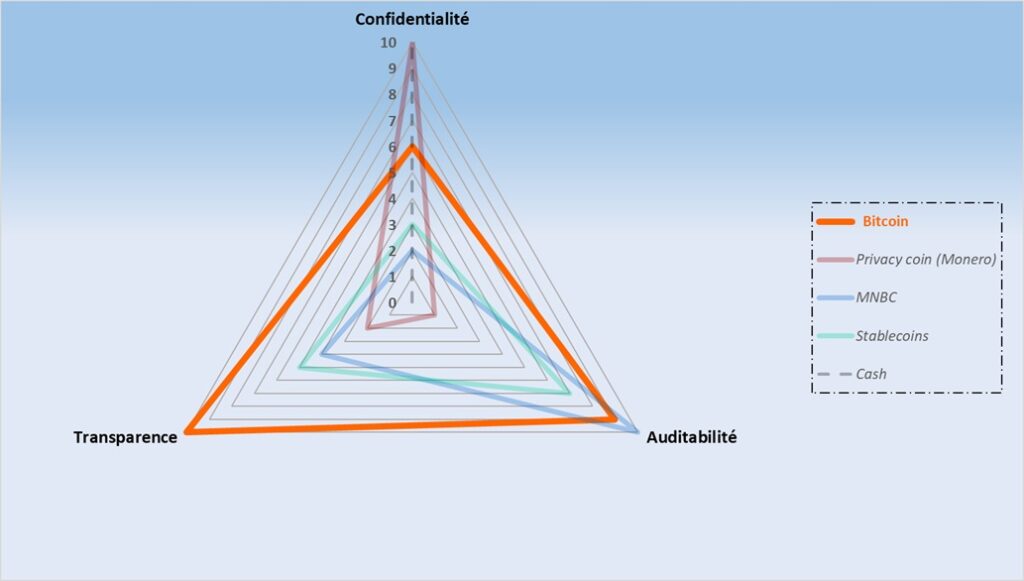
Bitcoin: Radical Transparency, Trust Guarantee at the Expense of Perfect Privacy
Between these two extremes, Bitcoin relies on a simple but decisive principle: making all transactions visible to anyone to prevent any manipulation of the monetary supply. This absolute transparency and auditability act as a bulwark against corruption, favoritism, and institutional abuses. They build trust in a system without a central authority. But this protective choice for protocol stability comes with very limited privacy. In an environment where every financial move becomes an interpretable signal, this permanent exposure is a real vulnerability. Bitcoin shows that transparency is an indispensable safeguard to guarantee system fairness while revealing an irreducible tension between total auditability and the fundamental right to privacy.
Bitcoin uses a simple pseudonymity based on cryptographic addresses (4A). These addresses hide civil identity (4B) but expose all financial behavior, like bank statements. Every transaction is recorded forever, which strengthens collective trust but weakens the novice user. A simple link between an address and a person is enough to reveal the full history. This vulnerability is further amplified by increasingly advanced analytical tools.
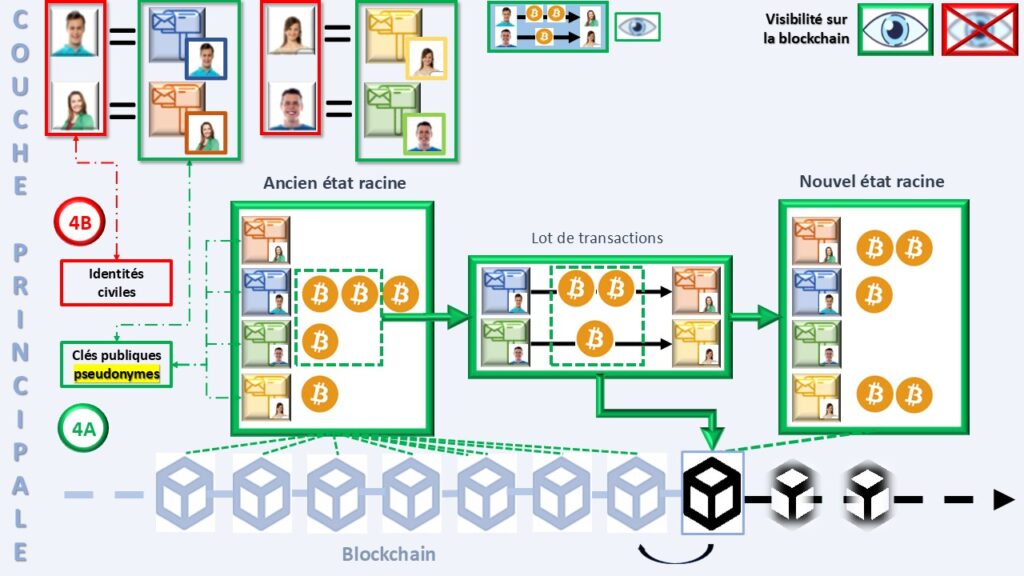
Pseudonymity creates a structural freedom because the protocol does not link real identities to transactions. This freedom limits censorship because no authority controls the unlimited creation of addresses. However, total transparency transforms any operational error into lasting privacy harm. Bitcoin maximizes overall system security but reduces individual private space. Its model reminds us that a perfectly transparent protocol cannot offer perfect privacy.
Key Success Factors of Digital Monetary Policy
A healthy digital monetary policy must natively incorporate selective privacy, able to reconcile regulatory compliance and individual protection. This approach allows compliance and transparency without sacrificing citizens’ privacy or weakening overall trust. It creates a space where money becomes ongoing social negotiation. Individuals demand freedom, while institutions demand security. Selectively privacy then becomes an essential adjustment variable between these opposing needs.
The main challenge is to resolve the structural tension between indispensable transparency and fundamental privacy. Bitcoin embodies monetary robustness but suffers from limited privacy. Monero guarantees strong anonymity but breaks with institutional standards. These two extremes reveal the limits of the “all-transparent” or “all-opaque” models. A credible monetary policy must ensure minimal individual sovereignty — protecting citizens against abusive surveillance — without abandoning the systemic auditability necessary for macroeconomic functioning.
Selective Privacy on Secondary Layers: The Client-Server Model Applied to Digital Currency
The most robust solution is to place selective privacy in dedicated secondary layers. The main layer of a network like Bitcoin remains transparent to ensure security, stability, and global auditability. Upper layers then add targeted privacy through advanced cryptographic mechanisms like rollups or off-chain networks. This model reinforces system reliability without complicating the infrastructure layer.
This structural separation balances privacy, security, and verifiability without creating extreme compromise. The main layer ensures collective trust while the secondary upper layers protect sensitive information. Authorities must share some power with these multi-layer cryptographic protocols. Citizens must benefit from native protections limiting any unjustified identification. This design strengthens individual freedom and preserves institutional stability.
This logic resembles the classic client-server model. The base layer acts as a robust server: transparent, minimalist, and security-centered. It verifies global rules without processing private data. Secondary layers function as smart clients. They mask complexity, optimize experience, and provide scalability, encryption, authentication, and privacy. Essential information rises to the main layer, but never intimate details.
This model avoids overloading the main layer and preserves operational privacy. It replicates Internet architecture, where secure services rely on a simple, stable base like TCP/IP. This modular structure balances transparency, performance, and individual protection coherently. It strengthens overall system resilience and reduces risks related to excessive centralization of the process.
Selective Privacy, a Necessary Compromise
Imagine an exclusive club where you must prove you know a password… without ever saying it. The doorman asks partial questions (the 3rd letter of the reversed password, for example). Answering correctly is enough to prove your right to enter without exposing the whole word. This is the essence of a cryptographic proof: showing that something is true without revealing the complete information.
Add a second rule. You present your ID, but only two elements remain visible: your photo and your birthdate. The rest is masked. The doorman can confirm your permission without accessing your privacy or personal information. This logic illustrates selective privacy: proving the essential, revealing the minimum.
This compromise finally reconciles security, privacy, and trust. It sets the foundation for a monetary model capable of functioning without turning every user into a permanent surveillance target.
1st Key Success Factor: Towards Selective Privacy with ZK-Rollups
The Zero-Knowledge rollup perfectly illustrates selective privacy applied to digital currency. This secondary layer aggregates transactions and sends only a mathematical proof to the main blockchain attesting that everything is correct. The blockchain thus only sees who deposits into the rollup and who withdraws to the main layer (6A and 6B). Like a doorman noting club entries and exits. However, it does not access amounts or private exchanges made inside (6C). Security remains intact, privacy is restored, and excessive surveillance loses its effectiveness.
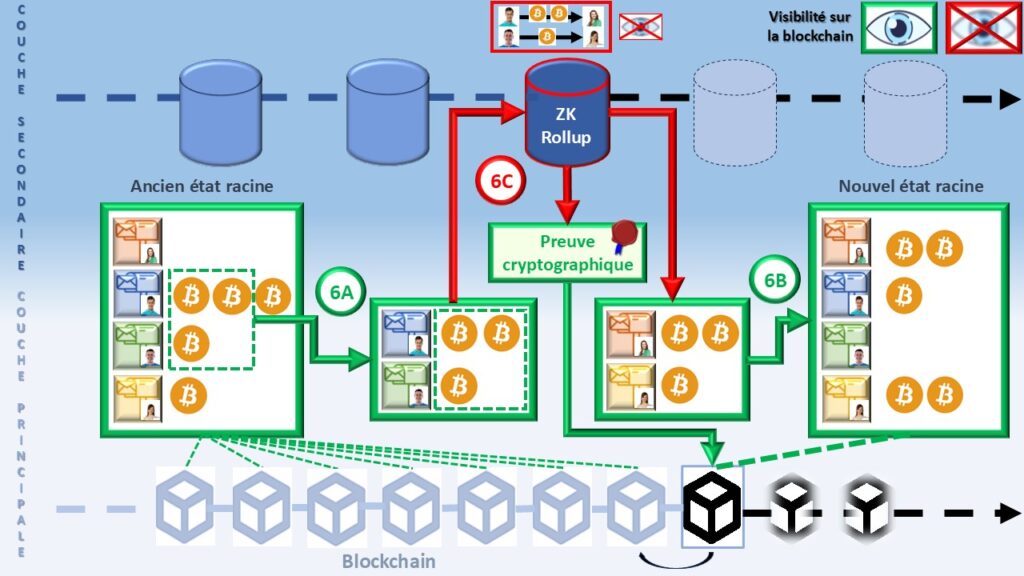
In a ZK-rollup, all transactions occur in an isolated space designed to protect sensitive data. The system then generates a unique proof, compact, that summarizes and validates all operations (6C). This zero-knowledge proof guarantees overall consistency without ever revealing details. The blockchain does not read transactions; it only verifies the proof and accepts or rejects the entire batch. This clear separation between public verification and private privacy creates a hybrid model. Transparency remains intact for network security, while privacy is preserved for each user. This architecture finally makes blockchain usable without permanent exposure. It concretely introduces selective privacy in daily digital exchanges.
Selective Privacy and Lightning Network: The Promise of a More Private Bitcoin
The Lightning Network, another example of an upper layer, offers selective privacy through off-chain payments. Only channel openings and closings appear publicly on Bitcoin’s main blockchain (7A and 7B). All internal transactions remain invisible to observers (7C). The whole functions like a receipt showing only the final total. The system never reveals each paid item. Onion routing hides the exact payment path. It also conceals the real amount and the full identity of the recipient.
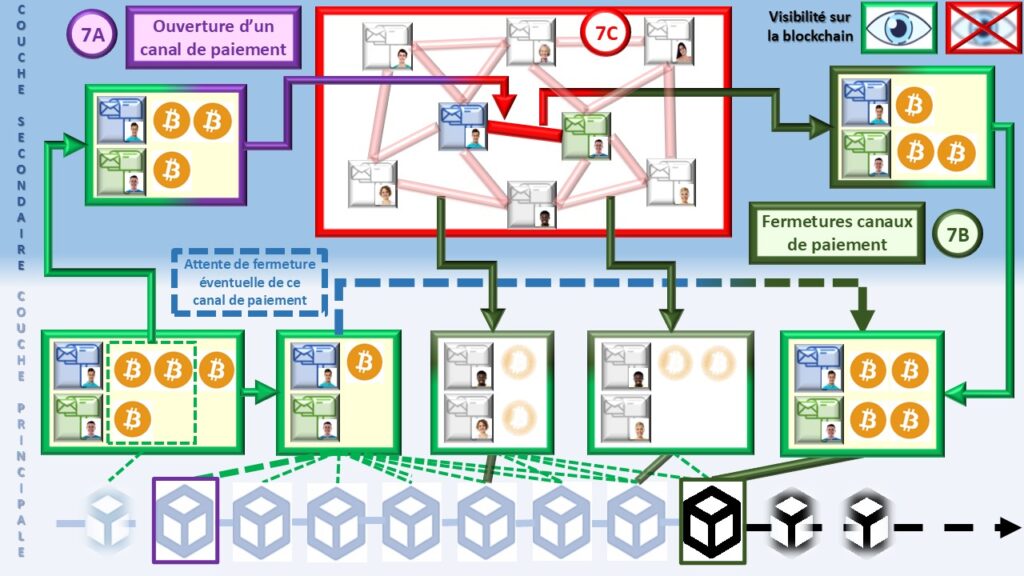
This protection remains imperfect, however. Channel openings and closings remain observable, and some adversaries can exploit volume or timing signals. Lightning does not aim for total opacity like Monero nor the cryptographic guarantees of ZK-rollups. It nevertheless protects the essentials for daily use. Buying a coffee does not require revealing a complete history. Lightning reduces on-chain analysis and enhances discretion. It improves resistance to abusive surveillance while preserving speed and low cost. These properties remain sufficient and optimal for a decentralized, efficient, and widely accessible network.
2nd Key Success Factor: The Right to Digital Silence
Beyond technological issues, the right to digital silence protects individual freedom in an environment that has become structurally all-seeing. Everyone should be able to interact without handing over their entire intimacy to systems. This principle corresponds to the modern equivalent of the legal right to silence used to avoid self-incrimination. The user must only prove what is strictly necessary for compliance. No action should generate information reusable against them. This logic reduces invasive data collection by public or private actors.
A free society requires preserved zones of personal opacity. Continuous surveillance must never become the implicit norm of digital environments. Collective security cannot justify imposed total transparency. This right also stands as a bulwark against institutional or commercial abuses. It restores autonomy space where everything encourages permanent disclosure. Silence thus becomes a fundamental right in a fully digitized world.
3rd Key Success Factor: Limited Public Auditability
Limited public auditability verifies system integrity without exposing individual identities or amounts. This principle creates a sustainable balance between collective transparency and personal confidentiality. A registry can remain publicly verifiable without turning every user into an accessible financial file. Bitcoin demonstrates that decentralized auditing works without continuous central supervision. This approach protects overall trust without compromising actors’ financial privacy. It prevents surveillance from becoming the implicit condition of economic compliance. Privacy remains compatible with robust and verifiable technical control. This model reduces institutional abuse risks linked to sensitive data. It limits potential impacts of large-scale leaks on citizen security. Limited public auditability consolidates system resilience and preserves individual freedoms.
4th Key Success Factor: Distributed and Transparent Governance
Distributed and transparent governance distributes power to avoid any excessive single authority. This model brings together banks, citizens, regulators, and developers in a truly shared process. It draws inspiration from Bitcoin’s decentralized consensus while respecting modern institutional constraints. This structure limits political arbitration risks that could undermine monetary stability. It strengthens decision legitimacy through diverse, independent voices. Privacy then becomes an essential pillar to ensure serene deliberations. It protects every actor from external pressures and unwanted manipulations. This framework prevents a single body from exploiting users’ sensitive data. It creates a decision-making space where transparency concerns rules rather than individuals.

5th Key Success Factor: Transparency of Rules
Rule transparency helps everyone understand the real functioning of a digital currency. Publishing codes, protocols, and privacy policies builds user trust. This openness directly draws from the open-source model established by Bitcoin from its inception. It ensures that monetary rules remain verifiable by everyone without advanced expertise. This transparency also protects citizens against invisible institutional abuses. Privacy then becomes an essential component of the overall educational framework. It prevents abusive exploitation of sensitive data behind opaque technical complexity. A system must clearly explain what it collects and why. Honest communication reduces information asymmetries between institutions and users. This principle sustainably strengthens a modern monetary system’s legitimacy.
6th Key Success Factor: Framed Censorship Resistance
Framed censorship resistance guarantees neutral transactions resistant to unwanted pressures. This principle protects the fundamental freedom derived from Bitcoin’s decentralization. It also incorporates minimal legal responsibility to preserve the rule of law. Ordinary transactions should not undergo arbitrary or political blocking. Judicial exceptions must remain strictly limited and firmly regulated. This framework protects citizens from unjustified economic censorship. Privacy prevents abuses based on sensitive personal data analysis. It limits opportunistic information exploitation by powerful actors. Partial censorship resistance consolidates trust without compromising collective security. This model reconciles individual freedom and proportionate legal obligations. It prevents any single authority from manipulating the system for opaque reasons. Framed censorship resistance thus becomes a key success factor for a resilient and fair modern currency.

7th Key Success Factor: Portability and Interoperability
Portability and interoperability ensure continuous privacy across distinct financial systems. They protect intimacy even when moving between different chains or digital environments. Transfers between CBDCs, private cryptocurrencies, or Web3 networks must retain the same protections. An open approach draws inspiration from interoperable Web3 standards and Bitcoin’s spirit. It prevents a technical transition from causing inadvertent leakage of sensitive data. Privacy then becomes a shared invariant rather than a fragile local property. This model limits cross-tracking by institutional or commercial actors. It avoids a system exploiting interoperability to collect additional information. Well-designed portability strengthens each citizen’s digital sovereignty. It guarantees smooth mobility between different forms of digital currency.
An Ideal Model Ultimately Leaning Towards Bitcoin… but Intelligently Regulated
Among all possible monetary architectures, Bitcoin remains the most accomplished example of a functional compromise. Its chain transparency prevents systemic manipulations and stabilizes its internal rules. The network remains resistant to political capture thanks to its lack of central authority. Native pseudonymity preserves minimal privacy to protect users’ private space. And secondary layers strengthen this privacy without weakening collective security. This model monitors structural abuses without turning individuals into permanent control targets. It reveals essential flows without exposing everyone’s economic intimacy. Bitcoin shows that a currency can be reliable without being intrusive. It proves a system can remain public without becoming punitive, and neutral without being blind. This balance offers a viable foundation for monetary policy respectful of society and the individual.
The ideal monetary policy adopts neither the total opacity of Monero nor the full surveillance of CBDCs. It instead emerges as a crypto-institutional synthesis inspired by Bitcoin’s design. Institutions find the verifiability needed to maintain stability and trust. Citizens retain sufficient privacy to protect their daily autonomy. Decentralized consensus guarantees impartial application of monetary rules. Operational transparency reassures observers without unveiling private financial life. Secondary layers effectively mask transactions using advanced cryptographic proofs. They offer robust privacy without encouraging uncontrollable criminal anonymity. This synthesis prevents panoptic drift while preserving economic accountability. It outlines a monetary architecture compatible with a mature digital democracy’s requirements.

Privacy as a Mirror of Power
Money always reveals the power that governs it. A trusting society verifies rules, not individuals. Transparency protects the system, but privacy constitutes the moral condition and the ethical safeguard of any transparency. Some modern technologies now offer protections impossible with cash. Multilayer architectures notably strengthen privacy without weakening systemic transparency. Financial privacy then becomes a technological right, not a political favor. Indeed, no institution should control citizens’ economic intimacy. Selective privacy prevents panoptic abuses and preserves creative freedom. It acts as a technological counter-power against the expansion of control systems. The more surveillance extends, the greater privacy’s value becomes. Choosing a digital currency thus means choosing a societal model. The issue goes beyond finance and directly touches human dignity. Like the chains evoked by Rosa Luxembourg.
Maximize your Cointribune experience with our "Read to Earn" program! For every article you read, earn points and access exclusive rewards. Sign up now and start earning benefits.

Consultant international en gestion de projet. Ingénieur de formation, avec une maîtrise en administration des affaires (M.B.A.) et affaires internationales d’HEC Montréal. Passionné de technologie et de cryptomonnaies depuis 2016.
The views, thoughts, and opinions expressed in this article belong solely to the author, and should not be taken as investment advice. Do your own research before taking any investment decisions.