A Massive Scam Organized by Pyongyang Hits GitHub, Upwork, and Freelancer
North Korean hackers have already siphoned millions in bitcoin and ether, ranking among the worst nightmares of the crypto community. Feared, hunted, cursed, they nevertheless evade every net. For recently, they no longer just steal: they recruit, organize, infiltrate, and structure. GitHub, Upwork, Freelancer… all platforms have become hunting grounds. And what they now aim at is no longer just a jackpot but the very framework of the decentralized economy.
In brief
- North Korean hackers impersonate recruiters and target freelancers on GitHub or Upwork.
- They use malware, forged documents, and AI to impersonate identities and deceive platforms.
- Victims are often vulnerable: women, Ukrainians, or precarious people lured by fake jobs.
- Payments pass through proxies and then go as crypto to the North Korean regime’s networks.
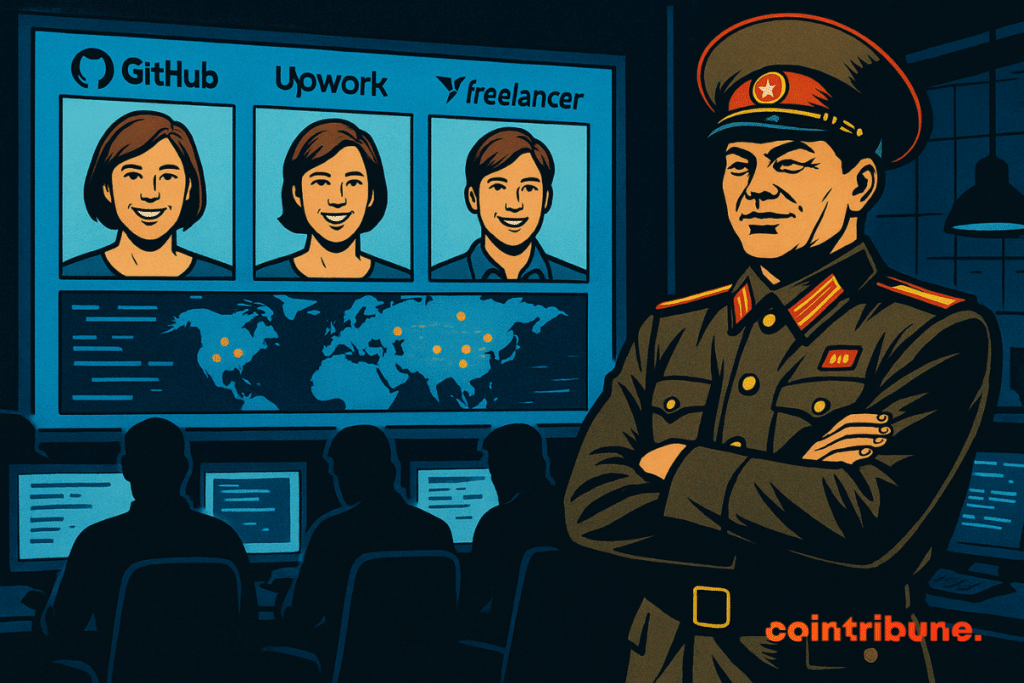
When AI Recruiters and Fake Profiles Infest Tech Platforms
In 2024, Pyongyang, which has more than 60 developers on crypto platforms, has taken a new step in its digital war. The regime’s hackers no longer simply apply for offers: they create them. On Upwork, Freelancer, or GitHub, they publish ads designed to lure developers specialized in crypto. Behind these seemingly ordinary offers lies a well-oiled plan: the candidate is invited to download a project hosted on GitHub, supposed to serve as a technical test. The code contains malware, often of the BeaverTail type.

To make these traps undetectable, North Korean agents use AI to generate faces, falsify voices, and produce ultra-credible official documents. They use sophisticated tools to enhance identity files, alter photos, and modify voices to deceive verification systems.
Nothing is left to chance: the appearance, the sound, the administrative details are optimized to pass checks without raising the slightest suspicion.
Require a live and interactive video interview during the selection process, to ensure the candidate’s appearance matches the profile photo and submitted documents (often stolen or AI-generated).
Heiner García Pérez, member of SEAL Intel
These fake profiles become real Trojan horses. The KYC system of platforms is no longer a barrier, but a camouflage tool. It’s a war of appearance where the North Korean regime leads the dance.
Social Engineering and Human Exploitation: Recruiters with a Digital Smile
North Korean cunning doesn’t stop at tools. It relies on human weaknesses. Pyongyang agents target vulnerable people: isolated freelancers, Ukrainians in crisis, women seeking economic independence. On forums like InterPals or AbleHere, approaches always start gently: a friendly exchange, a promise of income, a quick test.
Then comes the spiral: identity documents, software like AnyDesk, takeover of the freelance account. The “recruited” become fronts. And the share is clear: 20% for them, 80% for the operator.

An internal document found in a hacker’s files indicates a quasi-military organization: contact scripts, onboarding procedures, explanatory PowerPoint. Fraud becomes a digital subcontracting business.
The crypto community, which relies on decentralization, is the perfect prey. Digital wallets are accessible, crypto freelancers are numerous, identities circulate.
Behind this system, a chilling truth: Pyongyang exploits individuals to deceive others. And all this under a friendly, benevolent, almost engaging mask.
Opaque Networks, Crypto, and AI: Pyongyang’s Business Plan
What North Korea has set up amounts to an industrial plan. Payments pass through freelance platforms to bank accounts or crypto wallets held by “proxies.” Then, funds are repatriated in the form of crypto-assets to Pyongyang or its accomplices.
AI still plays a role here: generated profiles, simulated activity histories, fake Zoom calls to validate identities. Recruiters sometimes ask their collaborators to enroll their circle, forming a pyramid network hard to trace.
The crypto sphere becomes the ideal channel for these invisible flows: no bank, no regulator, no customs.
Visual Summary of Key Facts:
- More than 300 developers targeted since 2024;
- Payment redistributed according to a rule: 80% operator / 20% proxy;
- Infiltrated platforms: Upwork, Freelancer, GitHub…;
- Massive use of AI for identity theft;
- Widespread malware: BeaverTail, InvisibleFerret.
This model works because it mixes technology and psychological manipulation, with formidable effectiveness. Platforms, often overwhelmed, struggle to block these accounts, which reappear under other names, other faces.
North Korean hackers bled the crypto universe dry in 2024. With $1.3 billion siphoned, they signed a record year. Their strategy evolves. Their power too. How far will they go?
Maximize your Cointribune experience with our "Read to Earn" program! For every article you read, earn points and access exclusive rewards. Sign up now and start earning benefits.
La révolution blockchain et crypto est en marche ! Et le jour où les impacts se feront ressentir sur l’économie la plus vulnérable de ce Monde, contre toute espérance, je dirai que j’y étais pour quelque chose
The views, thoughts, and opinions expressed in this article belong solely to the author, and should not be taken as investment advice. Do your own research before taking any investment decisions.