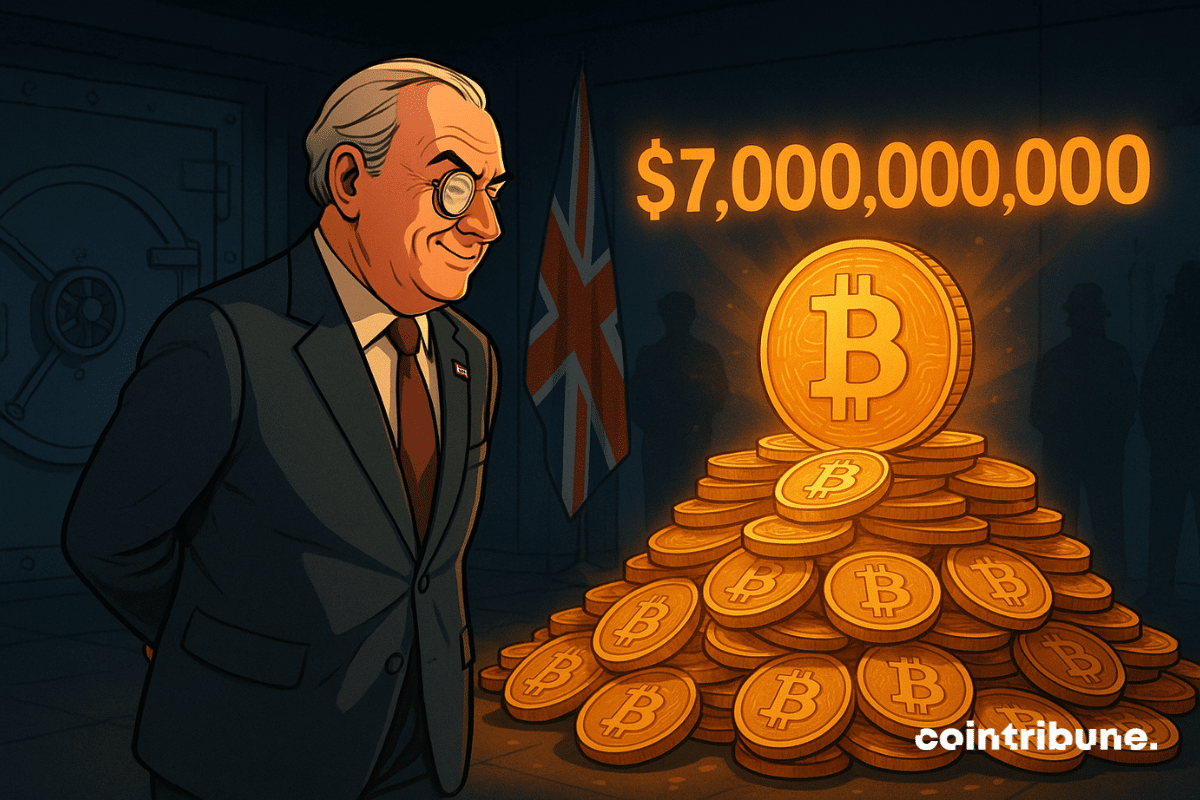
When London gets its hands on a treasure in bitcoin, it hesitates: justice for the victims or crypto jackpot for the Treasury? Who benefits from the digital crime?
Theme Cybersecurity
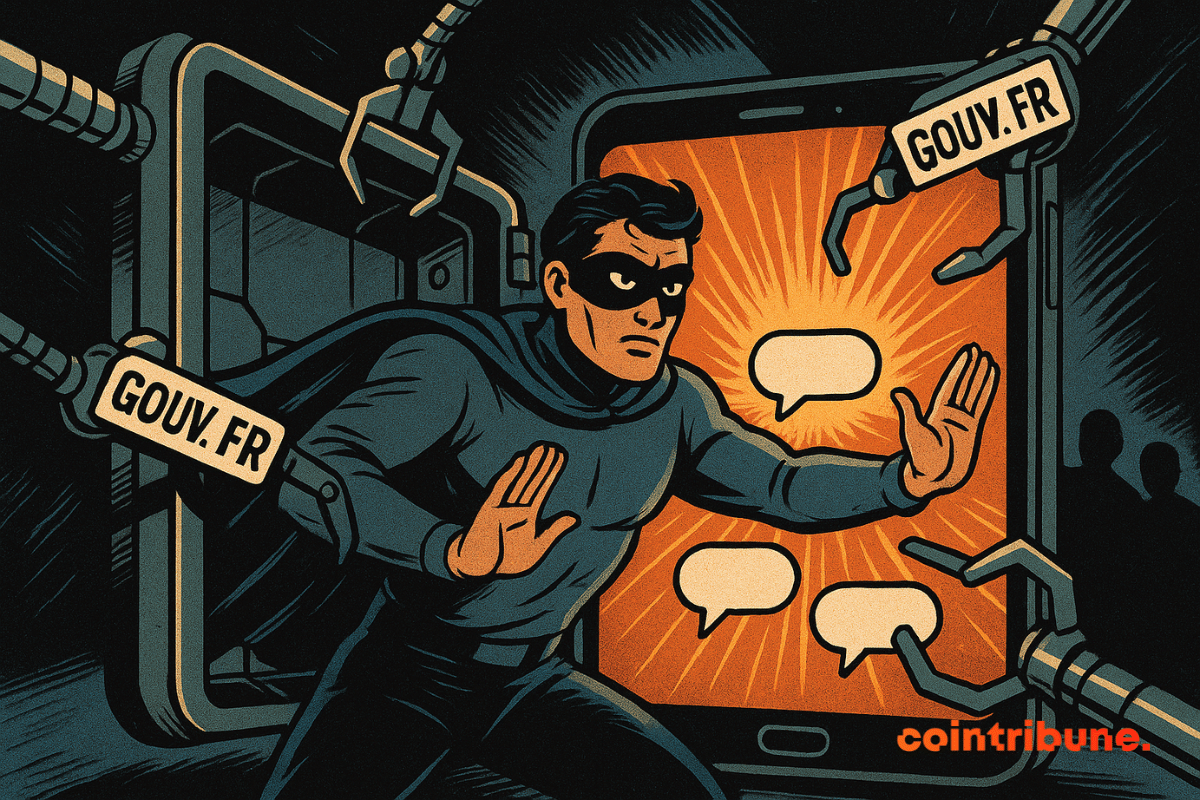
Pavel Durov breaks his silence and hits hard. The founder of Telegram claims that French intelligence services tried to force him to censor political content related to the Moldovan elections. A revelation that rekindles tensions between the messaging platform and French authorities. The case takes a worrying turn for freedom of expression in Europe.
The battle around "Chat Control" goes far beyond a simple technical issue. Behind this controversial law that the European Union is trying to pass is the very definition of digital privacy at stake. Vitalik Buterin, a major figure in crypto, has chosen to oppose it head-on, warning of a project with potentially explosive consequences.
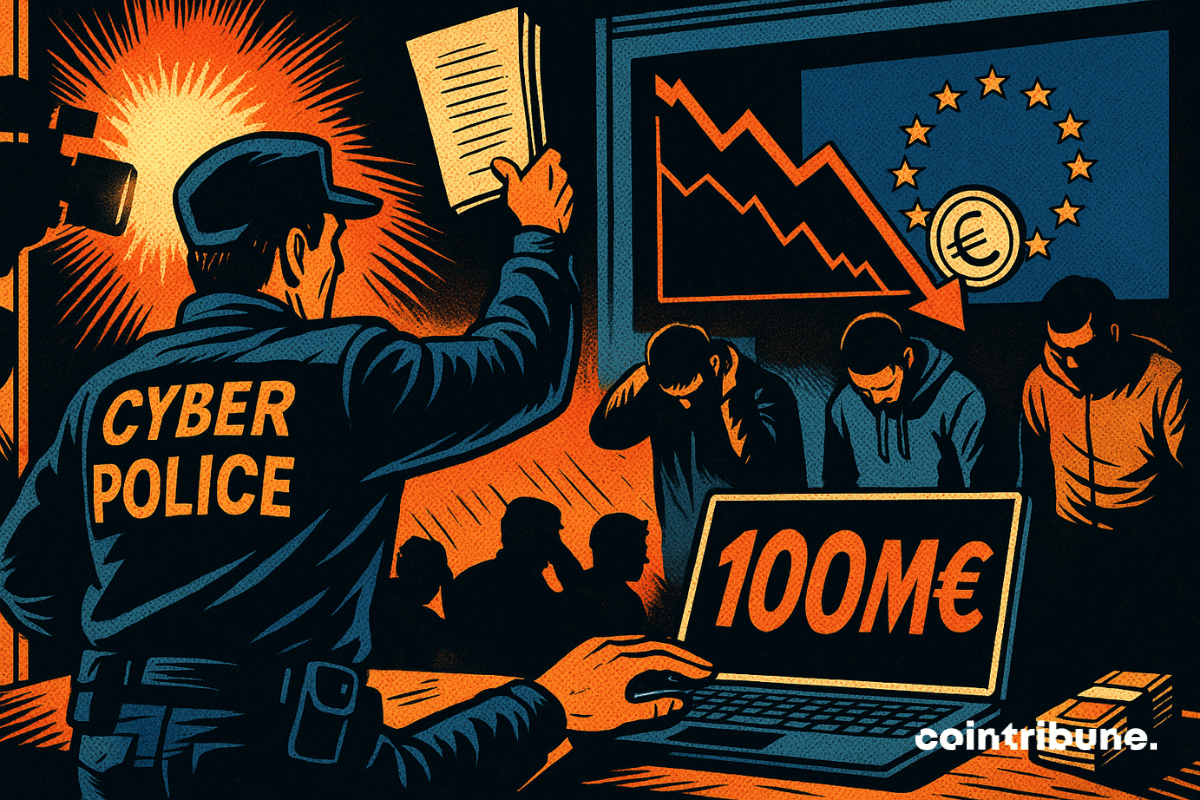
When cryptos become mirages, scammers become experts: 100 million stolen, 23 countries affected, 5 crooks arrested. And meanwhile, Bitcoin looks elsewhere, impassive.
The Crypto.com exchange finds itself at the center of a new cybersecurity case. According to Bloomberg, an attack carried out by a teenager and his accomplice allegedly allowed the disclosure of users' personal data. An episode all the more worrying as the platform reportedly chose to keep this breach silent.
X is taking legal action against banned accounts that tried to regain access through bribery and fraud, some of which are linked to the larger Com network under FBI scrutiny.
Infiltration in the crypto ecosystem: CZ denounces 60 fake developers linked to North Korea. All the details in this article!
What if bitcoin was racing against time? For Anatoly Yakovenko, co-founder of Solana, the advent of quantum computing is no longer a distant hypothesis. According to him, there is a 50% chance that a major breakthrough will occur within five years. A deadline that could obsolete bitcoin's current cryptography and force the market's leading crypto to urgently rethink its security architecture.
The U.S. Securities and Exchange Commission is reviewing a groundbreaking proposal that could reshape how the crypto industry prepares for quantum computing threats. The SEC is reviewing a groundbreaking proposal aimed at preparing Bitcoin and the wider crypto ecosystem for the looming threat of quantum computing, signaling that regulators are taking quantum risks seriously as experts warn "Q-Day" could arrive as early as 2028.
Less than twenty-four hours after the assassination of Charlie Kirk in Utah, the social network X was overwhelmed with messages calling for revenge and mentioning a civil war. Thousands of posts, often written in identical terms, point to the left as responsible. Faced with this surge, several researchers suspect artificial amplification. Behind these calls for violence, some accounts show characteristics of automated networks.
Apple’s iPhone 17, launched this month at a stable $799, is drawing attention for reasons beyond design and performance. For crypto holders, the device has suddenly become far cheaper in digital asset terms. Buyers now need only 0.0072 BTC or 0.1866 ETH to purchase it. That is almost half of what was required for the iPhone 16 a year ago.
The announcement by NIST (National Institute of Standards and Technology) regarding the selection of the HQC algorithm on March 11, 2025, as the fifth official post-quantum cryptography standard resonates as a warning signal for governments worldwide. This decision formalizes what cybersecurity experts have predicted for years: the rise of quantum computers represents a major quantum threat, capable of challenging the current foundations of cryptography and encryption. In this race against technological time, Naoris Protocol emerges as the first decentralized infrastructure able to meet the specific needs of public administrations and critical infrastructures.
A hijacked NPM account was at the center of a major supply-chain breach, putting the JavaScript ecosystem and crypto users at risk.
The crypto ecosystem has just suffered one of the most sophisticated attacks in its history. A "crypto-clipper" injected via compromised NPM modules quietly diverts wallet addresses during transactions. How did this breach escape security radars?
Quantum computer and Bitcoin. Here is a hot series that is not about to fade, especially after IBM's latest experiment.
In July 2025, a Microsoft vulnerability exposed over 400 public organizations, including the U.S. agency that manages the nuclear arsenal. Hospitals paralyzed, schools ransomed, and a post-quantum deadline now set: 2025 reminds governments that they won't win the cybersecurity race with late patches and centralized architectures. Faced with this reality, one question emerges: how do we build a truly resilient trust infrastructure?
A BNB whale fell victim to a $13.5 million phishing attack on Venus Protocol. The platform paused operations, but the stolen funds were later recovered.
A silent revolution is taking shape. As quantum computing becomes a reality, the very foundations of Web3 begin to tremble. Behind this invisible threat, a solution emerges: Naoris Protocol. A decentralized post-quantum cybersecurity infrastructure, it anticipates vulnerabilities that even nation-states fear. Its founder, David Carvalho, grants us an exclusive interview. An ethical hacker turned cyber strategist, he shares his vision, his technological choices, and his warnings. As the $NAORIS Token Generation Event (TGE) took place on July 31, 2025, a new paradigm is on the horizon..
What unbridled imagination for those coveting our cryptos! Each new episode of this long digital series redraws the contours of technological paranoia. The latest discovery? A simple image file. Yes, a doctored photo. Enough to turn your iPhone into a crypto sieve without you lifting a finger. The target? Everyone who uses Apple products… but especially, everyone who stores their wallet keys in unexpected places. Fortunately, an emergency update has been released to try to patch the breaches.
A new tool to check if your bitcoins are vulnerable to the quantum computer is now online. Are your BTC safe?
Global cybersecurity is facing an unprecedented challenge: organizations must simultaneously comply with NIS2, prepare for post-quantum migration (NIST 2030-2035 deadlines), and implement a truly operational zero-trust. This convergence of constraints creates a unique window of opportunity for solutions that solve multiple problems at once.
A group of crypto companies, financial institutions, and regulatory authorities has launched the Beacon Network. This network allows the rapid detection and freezing of stolen funds on the blockchain, bringing together players like Coinbase, Binance, Kraken, PayPal, and Ripple, alongside security researchers and law enforcement.
Embezzle 2 million, end up in prison, become a hero despite yourself... In crypto, even robbers become influencers. What if stealing was boosting business better than an airdrop?
The rapid rise of quantum computing revives fears of massive bitcoin hacking. Indeed, Microsoft’s revelation of its Majorana 1 chip, potentially capable of reaching one million qubits, fueled speculation about the end of the inviolability of private keys. However, Graham Cooke, former Google executive and now CEO of Brava Labs, dismisses these concerns. According to him, bitcoin cryptography remains out of reach, even for the most advanced machines.
The digital landscape is evolving within an increasingly complex, interconnected, and vulnerable environment. The emergence of quantum technologies, the rise of AI, and the proliferation of connected devices amplify existing vulnerabilities. Web2 and Web3 infrastructures still rely on centralized models that cannot withstand new threats. This centralization creates single points of failure and weakens overall system resilience. In light of this reality, a new approach becomes necessary. Naoris Protocol introduces the Cyber Physical Trust Mesh (CPTM), a decentralized, post-quantum infrastructure solution. It surpasses traditional DePIN by establishing a trust mesh designed to validate, secure, and continuously reinforce every digital layer.
Web2 enterprises today are on the brink of an extinction-level event. 'We've entered what I call the quantum danger zone,' states Dr. Richard Feynberg, Chief Science Officer at Quantum Shield Technologies. 'What was projected as a 2030 problem is now at our doorstep. I would be shocked if current encryption standards survive beyond mid-2026.' Their centralized infrastructures, already buckling under targeted attacks and invisible vulnerabilities, face imminent obliteration from quantum systems that are evolving at an exponential pace far exceeding even the most alarming predictions from just months ago. Traditional approaches are no longer sufficient to protect interconnected, complex, and critical systems. To address this challenge, Naoris Protocol offers a compelling alternative: a post-quantum, decentralized infrastructure designed to integrate seamlessly with existing environments. Operating above DePIN, it provides a continuous, distributed layer of security with no single point of failure. This article explores how Web2 enterprises can adopt this approach through practical, real-world integrations.
The cryptocurrency market continues to attract a growing number of investors seeking innovation and returns. Yet, each new attack or exploited vulnerability highlights the fragility of the ecosystem. Security remains a non-negotiable condition for sustaining trust and enabling mass adoption. A new vertical is emerging in response to these challenges: cybersecurity cryptocurrencies. These assets combine utility, resilience, and direct responses to the structural weaknesses of Web3. Among them, Naoris Protocol stands out for its infrastructure-first, decentralized, and post-quantum approach. This article explores current market risks, the importance of native security, and Naoris’s strategic role in this transformation.
The arrival of quantum computers isn't just shaking the foundations of global cybersecurity, it's triggering a seismic collapse that could happen any day. These machines, advancing at a pace that has shocked even the most conservative experts, now threaten to obliterate classical cryptographic systems within months, not years. 'The quantum earthquake is no longer a distant rumble, the ground beneath crypto is already cracking,' declares Professor Wei Chang of the Quantum Security Alliance. 'By this time next year, we could witness the complete compromise of blockchains, digital identities, and sensitive data on a scale unprecedented in digital history.' The window to prepare is closing with alarming speed. Centralized architectures, still dominant, show their limits when faced with these emerging risks. They concentrate vulnerabilities and lack both continuous validation and true resilience. In this context, a new generation of infrastructure is required. Naoris Protocol embodies this shift, going beyond traditional DePIN by introducing a post-quantum infrastructure layer called Sub-Zero. This architecture sits beneath Layer 0 and secures the entire digital ecosystem, from Web2 to Web3, through an autonomous, resilient mesh.
Web3 is expanding at breakneck speed, even as it races headlong toward a quantum cliff edge. 'The Web3 ecosystem is like a magnificent castle built on sand, with a tsunami visible on the horizon,' warns Dr. Samantha Torres, Director of the Quantum Cryptography Institute. 'Quantum systems capable of devastating current blockchain security could emerge as soon as Q3 2025, perhaps even sooner.' This imminent threat makes today's sophisticated attacks look like child's play. Smart contracts, bridges, and DEXs aren't just vulnerable targets, they're primed for complete compromise within months, not years, as quantum computing progress has shattered all previous timelines. Current cybersecurity solutions fail to offer long-term protection, relying on periodic audits and tools poorly suited for decentralized environments. To enable mass adoption, Web3 must integrate native, continuous, and future-proof security. Naoris Protocol offers a structural solution. It deploys a post-quantum, decentralized, verifiable infrastructure that goes beyond traditional DePIN. It introduces security embedded directly into the core architecture of Web3.
The transition to post-quantum cryptographic standards is becoming a global imperative. In the United States, authorities are mandating a migration by 2030, followed by the complete removal of current algorithms by 2035. In the face of this deadline, centralized infrastructures are showing their limits. It is in this context that Naoris Protocol stands out by proposing the first decentralized post-quantum infrastructure.